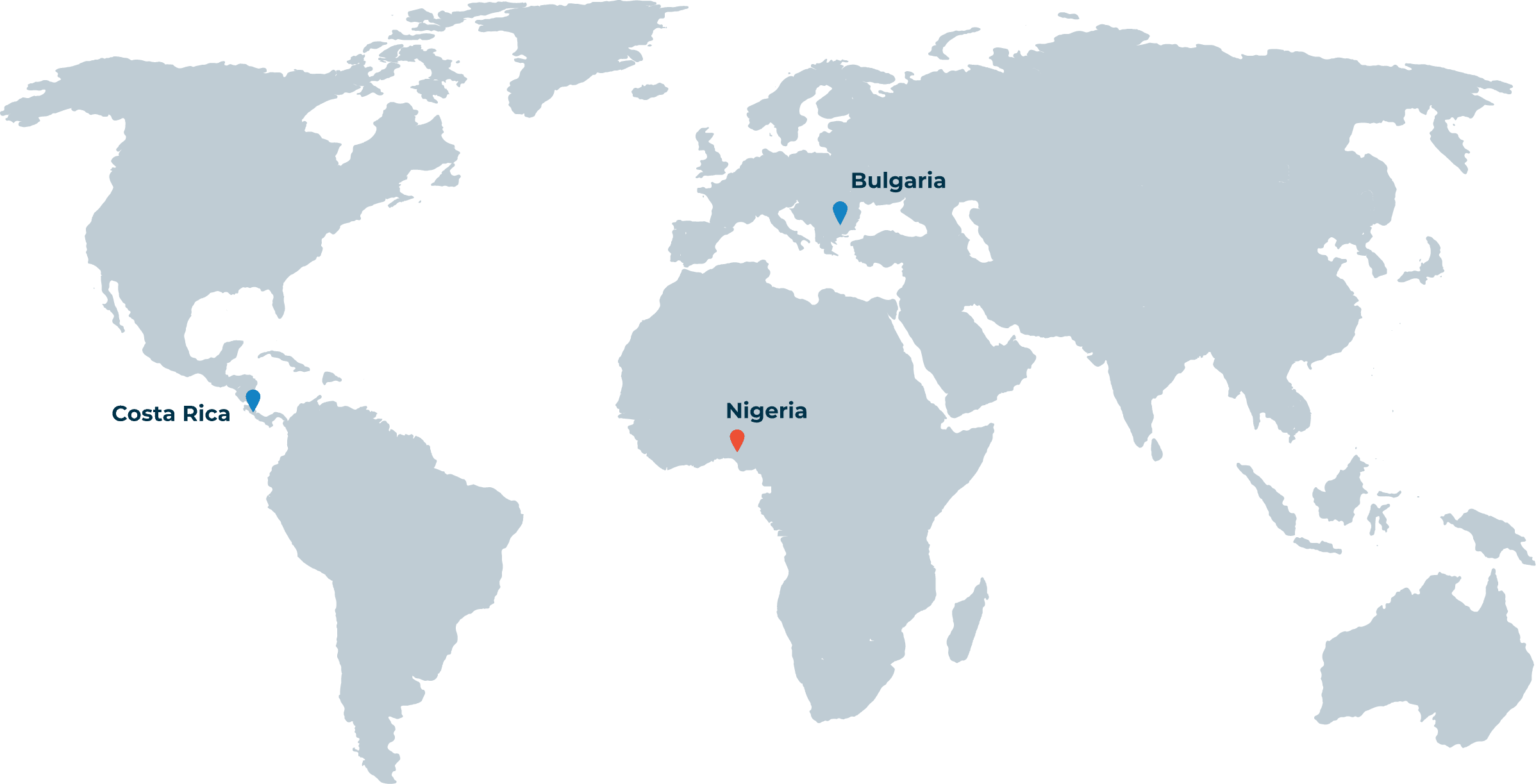
Managed Security Service Centers
24/7/365 Security Operation
Our international network of Managed Security Service Centers offers 24/7/365 follow-the-sun cybersecurity coverage to clients around the world.
In a world where digital landscapes evolve at an unprecedented pace, trust in security is paramount. As your trusted guardians, our Managed Security Service Centers stand as a fortress where cutting-edge technology converges with expert human vigilance to create a shield against cyber threats.
Backed by Microsoft’s industry-leading, Al-enabled Sentinel platform and operated by a team of cybersecurity experts, we deliver the full suite of cutting-edge cybersecurity solutions, providing round-the-clock protection. Take advantage of our dedicated team of cybersecurity experts and state-of-the-art technology to protect, monitor, detect, respond to, and mitigate the cybersecurity threats against your business, giving you peace of mind that your business has 24/7 protection to keep your organization safe in the face of multiple and ever-changing cyber threats.
24/7 Security Monitoring
We provide continuous real-time monitoring, detection, and correlation of data and alerts across your network - including all users and endpoints - from 'eyes on the glass' to after-hours to 24/7/365 coverage, depending on the extra resources you need to reduce the burden on your in-house team.
Real-Time Surveillance:
Around-the-clock monitoring of network traffic, system logs, and other security-related data to ensure uninterrupted security vigilance.
Advanced Analytics:
Utilization and optimization of the client tools to sift through vast amounts of data, pinpointing anomalies and potential threats.
Prompt Notification:
In the event of any suspicious activities or potential breaches detected, our team ensures immediate notification to the relevant stakeholders, facilitating swift action.
Investigation and Analysis
Our systematic process of examining and understanding security incidents, breaches, and potential threats provides our clients with deep insights into the nature of security events to devise effective strategies for containment, resolution, and deflection.
Alert Scrutiny:
Each security alert undergoes a rigorous examination process to validate its authenticity and potential impact.
Event Correlation:
Our experts adeptly correlate related events across your systems. This approach provides a holistic understanding of the security landscape and potential incidents.
Threat Contextualization:
We go beyond threat detection to further contextualize threats by integrating insights from global threat intelligence feeds to gain a deeper understanding of the broader implications of detected threats.
Threat Hunting:
Based on threat intelligence and other indications, we provide the solution for anticipating and mitigating cyber threats before they materialize into actual attacks.

Incident Response
Our on-demand team is ready to respond if a force majeure cyber incident comes into effect so your team has the support it needs to implement an instant, and effective, response plan and return to normal operations as quickly as possible.
Real-Time Response:
Upon detection of a security incident, our dedicated team will swiftly initiate predefined response protocols, ensuring timely containment, mitigation of threats, and a back to operation plan.
Stakeholder Collaboration:
Continuous communication with our clients ensures that all relevant parties are informed and aligned during the resolution process.
Quarterly Preparedness Drills:
To ensure optimal readiness and refine our response strategies, we conduct quarterly tabletop exercises (TTEs) and simulations. These drills not only test the effectiveness of our response mechanisms but also foster a culture of continuous learning and adaptation to evolving threat landscapes.

Security Operations (SecOps)
We provide continuous real-time monitoring, detection, and correlation of data and alerts across your network - including all users and endpoints - from 'eyes on the glass' to after-hours to 24/7/365 coverage, depending on the extra resources you need to reduce the burden on your in-house team.
Proactive Endpoint Detection And Firewall Maintenance:
Our expertise in managing endpoint detection and response (EDR) systems and firewalls ensures a robust defense against cyber threats. We proactively update and fine-tune these systems, optimizing your security landscape while reducing the need for extensive internal management.
Real-Time Support And Updates:
Keeping pace with the rapidly evolving cybersecurity landscape, we ensure your EDR and firewall systems are constantly updated. This ongoing vigilance shields your network from emerging threats, maintaining a secure and resilient environment.
Extended Security Controls Support:
We tailor our services to fit your unique security requirements, offering extended support for a diverse range of security controls. Our adaptable approach ensures that your specific security needs are met, enhancing your existing infrastructure seamlessly and effectively.
Local protection within a global network
Our Managed Security Centers and Security Operations Centers (SOC) provide 24/7 security. The distributed network of security centers leverages seamless handoff procedures, team transfer protocols, synchronization, and information exchange mechanisms to offer 24/7/365 follow-the-sun cybersecurity coverage to clients around the world.