Cyber threats keep getting more and more sophisticated. As such, organizations face the daunting task of safeguarding their digital assets against a myriad of potential attacks. It becomes mandatory for the enhancement of the cybersecurity posture to deploy a dedicated Security Operations Center (SOC) within the organization, serving as the central hub for monitoring, detecting, responding to, and mitigating security incidents.
Deciding to build a SOC internally is a key business decision, a strategic one really. Below, we will explore the challenges, and considerations involved in building your own SOC.
Understanding Security Operations Centers
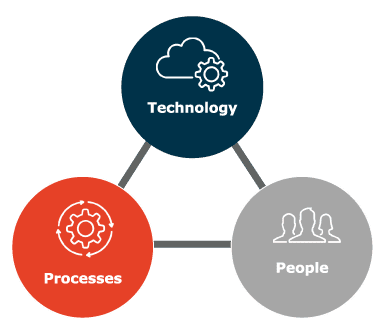
A SOC is a centralized unit responsible for continuously monitoring and improving an organization’s security posture. Its primary functions include threat detection, incident response, and proactive threat hunting. A well-designed SOC integrates people, processes, and technology to provide real-time insights into an organization’s security landscape.
Challenges in Building Your Own SOC
Setting up your own internal Security Operations Center might seem like the ultimate defense against cyber threats. Your data stays within your walls, expertise resides in-house, and control reigns supreme. Yet, it poses quite a few challenges.
Budget and resources
Establishing an internal SOC demands significant resources, both in terms of finances and skilled personnel. It’s an expensive endeavor. Salaries, tools, training, and infrastructure are heavy expenses, ongoing ones.
Cyber security skills and expertise
The cybersecurity talent pool is a shallow one. Acquiring and retaining talented cybersecurity professionals can be challenging due to the global shortage of skilled personnel in this field. Finding skilled analysts, threat hunters, and incident responders is difficult, and tempting experts to leave current places and move may come with a hefty price tag. Training personnel can also take time and resources, leaving organizational defenses vulnerable in the meantime.
Technological and integration requirements
Choosing and integrating the right technology stack is critical. The cybersecurity landscape is dynamic, and selecting tools that can adapt to emerging threats is paramount. Integration challenges may arise when attempting to connect disparate security technologies and platforms.
Regulatory compliance
Organizations operating in various industries must adhere to specific regulatory requirements. Building a SOC that aligns with these regulations, such as GDPR, HIPAA, or PCI DSS, adds an additional layer of complexity.
Who may benefit from an internal SOC?
While the challenges presented by internal SOCs are undeniable, certain organizational profiles stand to benefit significantly from its implementation. These include:
1. Enterprises with high-sensitivity data assets:
Organizations entrusted with data critical to national security, financial stability, or public health require the utmost vigilance and control over their infrastructure. This many times includes governments and givernmental agencies In such scenarios, the enhanced visibility and proactive threat detection capabilities of an internal SOC can mitigate risks and minimize potential damage from data breaches, justifying the investment.
2. Organizations with unique regulatory needs:
Some industries operate under strict regulatory frameworks. Establishing an in-house SOC allows organizations to tailor their security protocols to meet specific compliance requirements. This ensures that the organization remains in adherence to industry regulations, protecting sensitive data and avoiding legal consequences.
3. Cost-effectiveness for large enterprises:
For large enterprises dealing with massive volumes of data and numerous endpoints, the cost of outsourcing cybersecurity services can be substantial. Establishing an in-house SOC can be more cost-effective in the long run, as it allows for centralized control, scalability, and optimization of resources.
4. Companies with highly unique needs:
Some organizations have unique security requirements that may not be adequately addressed by generic cybersecurity solutions. In-house SOCs provide the flexibility to customize security measures, adapting to the organization’s specific risks, technologies, and operational practices. This tailored approach enhances the effectiveness of cybersecurity protocols and safeguards against evolving threats.
5. Companies with extreme sensitivity to real-time response:
Certain industries, such as critical infrastructure, and online services, demand real-time monitoring and response to potential threats. An in-house SOC, equipped with advanced technologies and skilled personnel, can provide immediate detection, analysis, and response to security incidents. This real-time capability is crucial for mitigating risks and minimizing the impact of cyber attacks on business operations.
Key considerations when building an internal SOC
Establishing an internal Security Operations Center (SOC) presents a compelling option for enhancing enterprise cybersecurity posture. However, it’s vital to undertake a comprehensive evaluation of the associated considerations before embarking on this potentially rewarding, yet resource-intensive, journey.
Aligning security objectives with business needs
The fundamental driver behind an internal SOC should be a defined and aligned set of organizational security objectives. It’s important to understand the organization’s specific needs, clearly define the objectives and scope of the SOC and tailor its functions accordingly.
Are you aiming for enhanced threat detection and incident response capabilities? Do you require centralized control over security data and infrastructure? Clearly articulating these objectives will guide subsequent resource allocation and technology selection decisions.
Assess Organizational Readiness
Evaluate the organization’s current cybersecurity maturity level and readiness for a SOC. This assessment helps in identifying gaps and determining the resources required for successful implementation.
Evaluating the ability and willingness to put in the needed resources
Building and maintaining an internal SOC demands significant commitment across three key resource areas:
- Talent: Skilled SOC personnel like analysts and threat hunters are in high demand and command premium salaries. Consider the existing skills within your organization and potential recruitment challenges. Also, be prepared to invest in ongoing training programs and continuous skill development to keep the team updated on the latest threats and technologies.
- Technology: Selecting and integrating the right security tools is crucial. Analyze your existing infrastructure, threat landscape, and budget constraints to determine the optimal technology stack. Choose technology solutions that align with the organization’s needs and are capable of integration. Prioritize technologies that facilitate automation and AI, threat intelligence sharing, and scalability.
- Infrastructure: An internal SOC necessitates robust IT infrastructure to handle data ingestion, analysis, and visualization. Assess your existing capabilities and potential upgrades required to support the SOC’s demands.
Understanding operational realities
Implementing an internal SOC requires meticulous planning and operational preparations:
- Incident Response Protocols: Establish clear and efficient incident response protocols to ensure timely and effective mitigation of potential threats. This includes effective communication channels, which are key in incident response, and are needed both within the SOC team and with other relevant stakeholders in the organization. Regularly test and update the plan to ensure its effectiveness.
- Threat Intelligence Integration: Leverage readily available threat intelligence feeds and integrate them into your SOC’s analysis capabilities for enhanced threat detection accuracy.
- Security Awareness and Training: Foster a culture of security awareness within your organization to complement the functionalities of the SOC.
Decide in advance on how to measure success
Defining key performance indicators (KPIs) for an internal SOC is crucial to track its effectiveness and identify areas for improvement. Regularly review and adapt processes, tools, and strategies to stay ahead of evolving threats and ensure the SOC remains aligned with the business objectives.
Cytek: Empowering organizational security posture with expert SOC guidance
At Cytek, we understand that no two organizations are alike. Hence, we offer a range of tailored SOC advisory and implementation services to fit the unique needs, risk profiles and budgets of our clients. Our cybersecurity advisory and implementation services empower organizations, accompanying them on their journey to build robust and resilient Security Operations Centers. Cytek offering includes:
Strategic cybersecurity advisory
- In-depth risk assessment and gap analysis: Conducting thorough assessments to identify potential vulnerabilities and assess the overall cybersecurity posture and gaps of the organization.
- Customized roadmap: Developing a tailored cybersecurity roadmap that aligns with business objectives, compliance requirements, and industry best practices.
SOC design and architecture
- Tailored SOC design: Creating a SOC architecture that meets the specific needs of the organization, considering factors such as size, industry, and regulatory requirements.
- Technology stack selection: Recommending the most appropriate cybersecurity technologies and tools to enhance threat detection, incident response, and forensic capabilities.
Implementation and integration
- Rapid deployment: Efficiently implementing the chosen cybersecurity solutions to minimize downtime and ensure a seamless transition to a more secure environment.
- Integration with existing systems: Seamlessly integrating SOC capabilities with the existing IT infrastructure to enhance overall operational efficiency.
- Integrating existing cyber security solutions: NO sunk costs.
24/7 monitoring and incident response
- Continuous monitoring: Establishing real-time monitoring capabilities to detect and respond to potential threats around the clock.
- Incident response planning: Developing and implementing robust incident response plans to minimize the impact of security incidents and ensure a swift recovery.
Training and skill development
- Employee training: Providing cybersecurity awareness training to staff to foster a security-conscious culture and reduce the risk of insider threats.
- SOC personnel development: Offering training programs for SOC personnel to ensure they stay ahead of evolving cybersecurity threats and technologies.
Performance metrics and reporting
- Key Performance Indicators: Defining and monitoring KPIs to measure the effectiveness of the SOC and to continuously improve its performance.
- Regular reporting: Providing comprehensive reports on cybersecurity incidents, threat landscape changes, and SOC performance to keep leadership informed.
We remain a trusted partner, post internal SOC building projects, offering our clients ongoing advice, expertise, and performance monitoring to ensure our clients’ SOCs continue to evolve and meet their needs over time.
Summary
Building an internal SOC is a strategic decision that demands careful consideration and a balanced approach. By understanding the resource requirements, operational realities, and ongoing commitment associated with this endeavor, organizations can make informed decisions about whether an internal SOC aligns with their security needs and long-term goals.
Organizations with resource and operational constraints may consider leveraging Managed SOC Services. These services provide access to a team of cybersecurity experts and advanced technologies without the need for a significant upfront investment.
