Going beyond the technology
We provide advisory, implementation, managed security services, and cybersecurity capability-building programs to help you combat new and existing cyber threats.
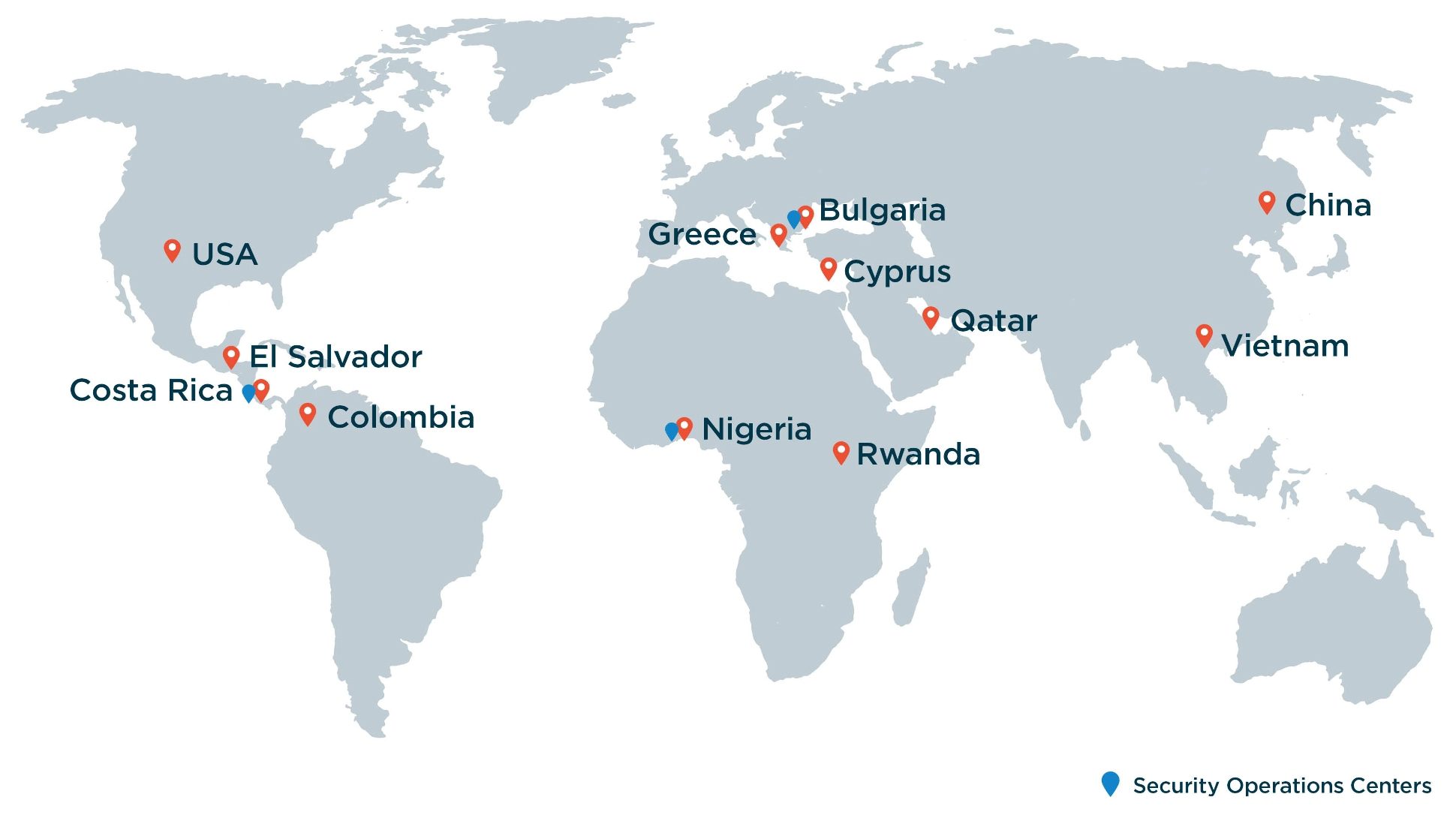
With our unique blend of worldwide security operation centers, rapid scalability, custom service design,and proprietary IP and methodologies that are based on our leadership’s years of experience delivering defense projects all over the world, we give you a much more efficient way to gain the cybersecurity coverage needed in today’s constantly evolving cyber threat landscape.
Support at every step
Whatever your cybersecurity (and business) requirements, our expert cybersecurity consultants start with a practical analysis of where you are now, where you need to get to, and the existing gaps. And we don’t just leave you to it. We provide the Advisory & Implementation, Managed Security Services or Capability Building you need to safeguard your organization.
-

Advisory & Implementation
Our advisory team identifies clear ways to improve your security posture and will design an implementation roadmap to help fill gaps as quickly as possible.
-

Managed Services
Our state-of-the-art managed services will continue to keep your organization safe in the face of multiple and ever-changing cyber threats.
-

Capability Building
Deploy our cybersecurity capability building programs, including a fully operated, dedicated, organizational cybersecurity Center of Excellence, labs and simulators, leveraging our proven methodologies for building cyber DNAs.
Cytek and Tek Experts launch a new SOC in Nigeria
The Security Operations Center (SOC) will be hosted by Tek Experts in Lagos and operated by Cytek’s team of cybersecurity experts. Built on a solid and innovative methodology, the SOC leverages Microsoft’s Al-powered technology to pinpoint and investigate cyber threats at a pace that far exceeds human capability.
TELL ME MORE

WHY US?
Peace of mind
In a constantly shifting cybersecurity landscape, it isn’t easy to stay on top of the latest threats with an in-house team. This is the challenge that Cytek solves with its state-of-the-art cybersecurity solutions, delivered by the world’s top cybersecurity experts.
We don’t just use state-of-the-art technology; we leverage our teams’ extensive track record in establishing and managing numerous national-level and highly classified cyber defense projects, to help organizations and governments enhance their cybersecurity posture and effectively combat new and existing cyber threats.
Our unique blend of Security Operation Centers (SOC) worldwide, rapid scalability, custom service design, and proprietary IP and methodologies assure convenient augmentation of internal resources, while enjoying top notch, extensive security coverage in the most efficient, cost effective manner.