ABOUT US
Cytek Security provides state-of-the-art cybersecurity solutions, delivered by the world’s top cyber experts. This includes advisory and implementation services, managed security services, and capability building.
Organizations today navigate a treacherous digital landscape, where valuable data and critical operations are constantly under siege by ever-evolving cyber threats. The pressure is on to fortify defenses, and Artificial Intelligence (AI) emerges as a potential game-changer, offering immense potential as a tool for proactive defense. However, in the wrong hands, AI can turn into a formidable foe. The cyber battlefield is becoming increasingly complex, demanding a nuanced understanding of AI’s potential, both as a shield and as a weapon.
This white paper provides a critical exploration of AI in cyber security. In it, we dissect the immense defensive capabilities of AI, unveil its potent threats and ultimately chart a course towards leveraging its power responsibly.
AI: Revolutionizing industries with its superpowers
AI’s enormous potential lies in its ability to surpass human capabilities in several key areas. First and foremost, AI’s speed and scalability are unmatched. AI algorithms can analyze vast amounts of data in milliseconds, identifying patterns and anomalies that would take humans years to detect.
Beyond speed, AI excels at Natural Language Processing (NLP), understanding and extracting meaning from human language with remarkable accuracy.
Furthermore, AI boasts the unique ability for continuous learning. Like a tireless student, it evolves with every interaction, refining its detection models and adapting to new circumstances and conditions.
Additionally, AI can break down language barriers, operating multi-lingually. It can analyze data and threats in various languages, providing comprehensive capabilities regardless of the attacker’s or defender’s origin.
Ultimately, AI’s unique capabilities make it a formidable ally in the fight against cybercrime, offering a level of defense that human analysts alone simply cannot achieve. Let’s explore some more.
AI in cyber defense: Challenges to consider
While AI presents exciting possibilities for bolstering cyber defenses, it’s crucial to acknowledge the challenges it introduces. Just like any powerful tool, its effectiveness hinges on responsible use and understanding its limitations. Let’s discuss some issues that may arise when using AI in cybersecurity defense.
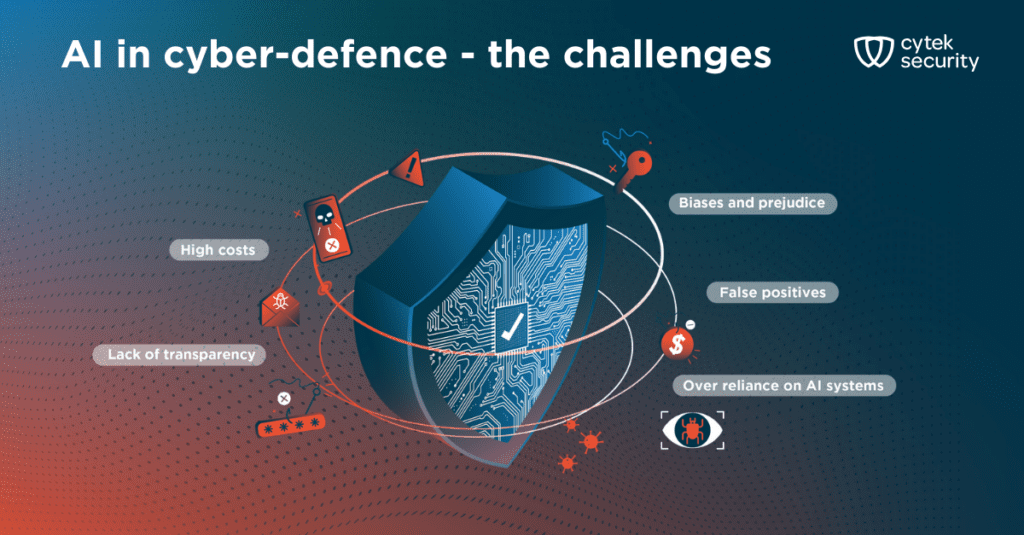

To start, when using AI, false positives are something that has to be taken into account. The fact that a certain detection is coming from AI engine does not make it immune to being a false positive. Imagine a scenario in which a security team is being bombarded with constant alarms triggered by AI, only to discover most are false positives. This “alert fatigue” can overwhelm security personnel, diverting valuable resources from investigating genuine threats. Balancing sensitivity with accuracy is crucial to ensure AI serves as a valuable ally, not a nuisance.
Also, AI models excel at pattern recognition and anomaly detection, but in most cases, their decision-making process is not fully transparent. This lack of transparency can make it difficult to understand how and why a specific threat was flagged, hindering efforts to refine the model and ensure its correctness.
Next, it’s a known fact that AI models are biased. They are only as good as the data they’re trained on. If the training data harbors biases, the model can inherit and perpetuate them, leading to discriminatory outcomes. Careful data selection and bias mitigation techniques are essential to ensure AI serves justice, not prejudice.
Cost-effectiveness is also an issue to be considered. Implementing and maintaining complex AI systems requires significant investment, both in terms of financial resources and technical expertise. Smaller organizations may find this barrier to entry insurmountable, potentially widening the security gap between different entities. A managed Security Operations Center (SOC) can serve as a great solution in these cases, allowing smaller organizations to still enjoy all that AI-assisted cyber defense has to offer. We’ll go into more detail about that later.
While AI excels at automation and pattern recognition, human judgment and critical thinking remain indispensable. Overreliance on AI solutions without proper human oversight can be misleading and cause us to neglect crucial details or overlook emerging threats that require nuanced interpretation.
By acknowledging these challenges and proactively addressing them, we can harness the true potential of AI in cyber defense while mitigating its risks.
AI’s defensive toolbox: Bolstering defenses across the cybersecurity spectrum
For defenders in the ever-escalating cyber war, Artificial Intelligence (AI) has emerged as a powerful ally, wielding a unique set of skills that bolster defenses and turn the tide against attackers. The most popular AI-enhanced cybersecurity practices include:
- Enhanced threat detection and analysis. An AI-powered IDS/IPS system is like having a tireless security analyst meticulously scrutinizing every corner of the organization’s digital landscape. AI algorithms sift through massive amounts of data such as system logs and network traffic, to uncover hidden patterns and anomalies that might indicate an impending attack and potential intrusions. They excel at recognizing subtle deviations from normal behavior, even those cleverly disguised by attackers, allowing defenders to proactively address threats before they materialize. They also adapt to evolving attack patterns and learn from past incidents, offering proactive threat detection and prevention capabilities.
- Phishing and social engineering detection. Social engineering and phishing attacks often rely on manipulating human emotions and exploiting trust. Luckily, AI can see through these elaborate deceptions. AI’s language processing prowess can be leveraged to analyze emails and messages, recognizing suspicious wording, sender behavior, and even subtle visual cues that betray fraudulent attempts.
- Smart AI-based support systems can automate repetitive tasks and guide security personnel through complex incident response procedures, saving valuable time and resources.
- Automated response systems. In a case where a security breach occurs, each second counts and the clock ticks as defense teams scramble to contain the damage. AI-powered systems can automatically trigger countermeasures like blocking suspicious IP addresses or quarantining infected files upon threat detection, minimizing potential damage. This swift intervention can make all the difference and can significantly limit the impact of an attack.
- Threat intelligence. AI automates data analysis from various sources, including dark web and threat feeds. Advanced analytics analyze past attacks and attacker behavior to predict future trends, uncover hidden connections, prioritize high-risk threats, and predict future attack vectors, empowering proactive defense strategies.
- Continuous learning and adaptation are extremely beneficial as attackers constantly devise new tactics and exploit novel vulnerabilities. Unlike traditional security solutions, AI models possess the remarkable ability to continuously learn and adapt. As they encounter new threats, they refine their detection capabilities, ensuring defenses remain agile and effective against even the most sophisticated adversaries.
- Vulnerability identification and prioritization are all about having a prioritized list of vulnerabilities, highlighting the ones that pose the most immediate risk. AI-based tools excel at performing this critical task, meticulously scanning organizational systems to identify and rank vulnerabilities based on their potential impact and exploitability. This allows for effective resource allocation, keeping the focus on patching the most critical vulnerabilities first and minimizing attack surfaces.
- Anti-malware and antivirus software. Traditional signature-based detection struggles with ever-evolving malware. AI-powered solutions leverage behavioral analysis and machine learning to identify and neutralize even zero-day threats, providing real-time protection against constantly morphing malicious software.
- Security information and event management (SIEM) & security orchestration, automation, and response (SOAR). AI fuels these integrated platforms by ingesting and analyzing data from diverse sources, correlating events, and identifying complex security incidents. SOAR leverages AI for automated responses, streamlining incident resolution and minimizing damage.
- User and entity behavior analytics (UEBA). UEBA leverages AI to analyze user behavior patterns and entity activity across systems. This includes detecting unusual login attempts, file access anomalies, and communication with suspicious entities, helping identify potential insider threats and data breaches early on.
- Fraud detection and prevention. AI models trained on historical fraud patterns can analyze transactions and user behavior in real time, identifying suspicious activities like unauthorized access attempts, money laundering attempts, or fraudulent account creation. This proactive approach mitigates financial losses and protects sensitive data.
- Data loss prevention (DLP). AI-powered DLP solutions go beyond traditional keyword matching. They analyze data content, context, and user intent to identify sensitive information at risk of unauthorized exfiltration. This prevents accidental or malicious data leaks, safeguarding intellectual property and customer privacy.
It’s important to remember that AI is a powerful tool, but not a magic bullet. Its effectiveness relies on high-quality data, clear objectives, and continuous improvement. By responsibly integrating AI into these diverse defensive areas, organizations can build a more robust and adaptable cybersecurity posture.
The Dark side of the moon: How attackers wield AI in cyber warfare
While AI presents a powerful tool in the hands of cybersecurity defenders, it’s crucial to acknowledge its potential misuse by malicious actors. In the wrong hands, this technology can become a sophisticated weapon, capable of supporting devastating attacks that exploit human vulnerabilities and bypass traditional defenses. Let’s delve into some of the ways AI can be weaponized


1. The art of deception: Personalized phishing
A scenario in which an employee is receiving an email that appears to be from a trusted colleague, perfectly mimicking their writing style and referencing specific details about joint work, becomes possible with AI-powered phishing attacks. These malicious programs can analyze vast amounts of personal data, crafting highly targeted emails that bypass traditional spam filters and exploit victims’ trust.
2. The shape-shifting threat: Autonomous malware on the loose
Traditional malware often generates static signatures that allow security software to detect and neutralize it. But what if malware could learn and adapt? AI-powered malware can do just that, analyzing its environment and modifying its behavior to evade detection. For example, attackers can develop malware that actively hides its presence within infected systems. These sophisticated programs can manipulate system logs, disrupt security software, and even camouflage themselves as legitimate processes. This “living” threat poses a significant challenge, demanding innovative defense strategies.
3. Lies that seem real: Deepfakes and disinformation campaigns
The ability to create realistic fake videos and news articles using AI, known as deepfakes, raises serious concerns. Malicious actors can leverage this technology to wreak havoc, manipulate public opinion, and even damage reputations. A simple example can be a deepfake video of a CEO making false statements, causing chaos in the financial markets. Another example can be a voice deepfake that is used to bypass an MFA solution for a bank.
4. Social engineering 2.0: Automating manipulation
We already mentioned social engineering, the art of exploiting human trust and emotions. This is a common tactic used by cyber attackers, which AI can take to a new level – automating tasks like crafting personalized messages, identifying vulnerable individuals, and even mimicking human conversation patterns. This harsh prospect highlights the need for increased awareness and critical thinking skills to counter such attacks.
5. Breaking down the wall: Password cracking
Brute-force password attacks involve trying countless combinations until the correct one is found. AI can significantly accelerate this process by implementing, among other measures, predictive analytics, and improving brute force techniques. This emphasizes the importance of strong, unique passwords and multi-factor authentication to thwart such attempts.
6. Poisoning the well: Data poisoning attacks
Imagine feeding false or manipulated data into machine learning models used by organizations for various purposes. This practice, known as data poisoning, can have severe consequences if left unchecked. Attackers can use AI to generate and inject such poisoned data, compromising the integrity of models and potentially leading to disastrous outcomes.
7. Scouting the territory: AI-powered reconnaissance
Before launching a major attack, attackers often engage in reconnaissance, gathering information about their target’s systems and vulnerabilities. AI can automate this process, analyzing vast amounts of publicly available data and even actively probing networks for weaknesses. This highlights the importance of maintaining strong network security and being mindful of what information is shared publicly.
The integration of AI into attacker arsenals poses a chilling prospect. Not only could it enable the development of more complex, sophisticated and targeted attacks, bypassing even robust defenses, but it could also democratize cybercrime and lower the barrier to entry, meaning that even less skilled individuals may use AI-powered tools to launch sophisticated attacks with relative ease. This democratization of cybercrime opens Pandora’s box of potential threats, exponentially increasing the attack surface defenders must contend with.
Let’s better understand this battle of the forces using a practical example – a ransomware attack.
The AI ransomware showdown: Attack vs defense
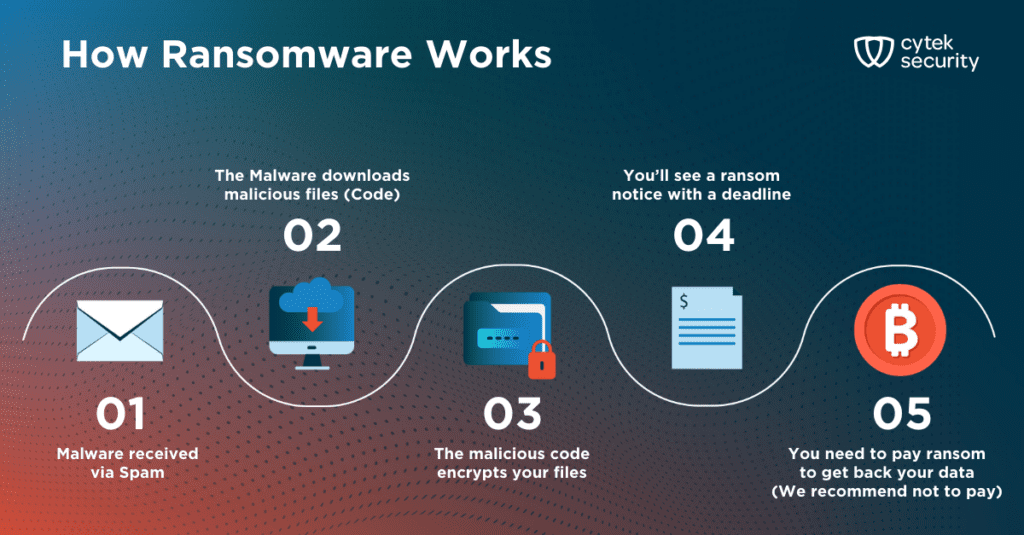

Scenario: In our example, a leading financial services, traded company that naturally stores sensitive data and relies heavily on its interconnection with many other entities. A sophisticated cybercriminal group plans a multi-pronged ransomware attack using AI.
Attacker’s AI arsenal
Personalized phishing: Our group employs AI to analyze social media profiles and internal emails of the company’s key personnel. Tailored phishing emails, mimicking communication style and referencing specific projects, are sent, targeting individuals with access to critical systems.
AI-powered malware: The phishing emails contain malicious attachments. Upon opening, the AI-powered malware adapts to the victim’s system, exploiting specific vulnerabilities and evading traditional signature-based detection.
Deepfake CEO: Simultaneously, a deepfake video of the company’s CEO surfaces online, demanding ransom and threatening to leak sensitive data. This sows panic and weakens public trust.
Social media manipulation: In parallel, bots powered by AI flood social media with negative comments and misinformation, further pressuring the company to comply with the attacker’s demand.
Lateral movement and data exfiltration: The malware grants remote access, allowing our group of criminals to move laterally across the network, identifying and exfiltrating valuable data using AI-powered data extraction tools.
Defender’s AI shield
Anomaly detection: AI-powered systems analyze network traffic and user behavior, detecting deviations from normal patterns triggered by phishing emails and malware activity.
AI-driven threat hunting: Upon anomaly detection, AI algorithms analyze vast amounts of data logs, identifying the root cause of the attack and the specific malware used.
Automated containment: The AI system automatically isolates compromised systems and restricts lateral movement, preventing further data exfiltration.
Deepfake detection: Advanced AI models trained on deepfake characteristics analyze the CEO video, identifying inconsistencies and flagging it as a fabrication.
Social media monitoring: AI-powered sentiment analysis tools track social media trends, identifying and countering misinformation campaigns orchestrated by malicious groups’ bots.
Data backups and restoration: Regularly backed-up data, protected by immutable storage solutions, are readily available for restoration, minimizing the impact of data exfiltration.
The outcome
The company’s AI-powered defenses successfully detect and contain the attack, minimizing data loss and operational disruption. The deepfake is exposed, and social media manipulation attempts are countered. While our cybercriminals might adapt their tactics, The company’s continuous improvement of its AI defenses ensures a resilient posture against future AI-powered threats.
Next, let’s explore how AI empowers two specific areas that are critical in today’s organizational cyber defense: The cybersecurity skill gap and managed SOCs.
The role of AI in bridging the cybersecurity skill gap
The cybersecurity industry faces a persistent and significant skill gap, leaving organizations vulnerable to attacks. AI presents several promising opportunities to address this talent shortage and empower security teams:
Automating repetitive tasks
SOC analysts often spend valuable time on mundane tasks like log analysis and threat detection. AI-powered tools can automate these repetitive processes, freeing up analysts to focus on higher-level strategic thinking, incident investigation, and threat hunting. This not only enhances their efficiency but also increases job satisfaction and reduces burnout.
Democratizing security expertise
AI-powered security solutions can offer guided assistance to analysts, even those with limited experience. By suggesting relevant playbooks, providing context-specific knowledge bases, and highlighting potential leads, AI can bridge the knowledge gap and empower them to make informed decisions even without extensive cyber expertise.
Upskilling the workforce
Continuous learning is crucial in cybersecurity. AI-powered training platforms can personalize learning experiences for analysts, identifying their knowledge gaps and recommending relevant courses, tutorials, and simulations. This adaptive approach ensures they stay up to date with the latest threats and techniques, closing the skill gap over time.
Identifying and recruiting talent
AI can analyze vast amounts of data to identify individuals with skills and aptitudes suitable for cybersecurity roles. This can help organizations recruit more effectively, tapping into hidden pools of talent that might not have traditionally considered a career in cybersecurity.
Some concerns exist about AI perpetuating biases in recruitment and decision-making or creating overreliance on automated systems. Indeed, AI can play a significant role in addressing the cybersecurity skills gap, however, its successful integration requires careful consideration of ethical implications and a focus on human-AI collaboration to ensure a secure and empowered future for the cybersecurity workforce.
AI powers up the managed SOC: Security operations overhauled
Security Operation Centers (SOCs) play a critical role in safeguarding organizations against an ever-evolving cyber threat landscape. As attackers increasingly leverage Artificial Intelligence (AI) in their arsenal, it’s crucial for SOCs to adopt this game-changing technology to stay ahead of the curve. Managed SOCs, offering expertise and resources to various organizations, can leverage AI to significantly enhance their capabilities in several key areas.
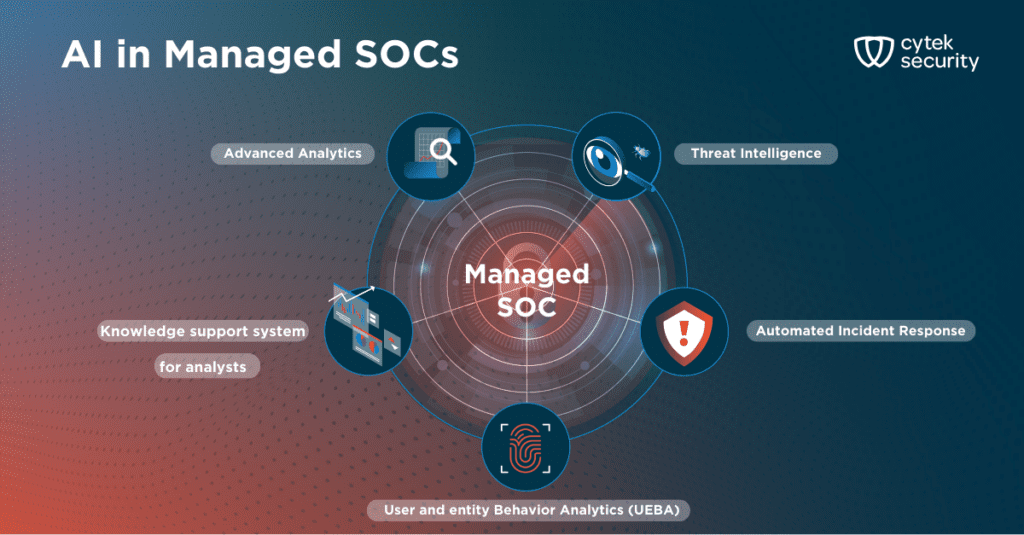

By integrating AI into their operations, managed SOCs can unlock a new level of efficiency, speed, and accuracy in detecting, investigating, and responding to cyber threats. This not only benefits individual organizations but also strengthens the overall cyber security posture of the broader ecosystem. AI-powered managed SOCs also offer smaller organizations an opportunity to leverage everything that AI defense has to offer, for a reasonable price tag, helping to keep the security gap between different entities at bay.
Summary
At the end of the day, we are currently in a place where the arms race between attackers and defenders intensifies, as each side leverages AI to outmaneuver the other. This escalating battle underlines the urgent need to establish clear protocols for human oversight and accountability.
It’s important to remember that AI is a tool, not a silver bullet. Its effectiveness hinges on robust data quality, clear goals, and continuous improvement strategies.
The path forward lies in responsible development, ethical implementation, and a clear understanding of both the immense power and inherent limitations of this transformative technology. This is crucial for building trust and ensuring public acceptance of AI-powered solutions.