Incident response and mitigation are critical components of any Security Operations Center (SOC) service offering. When the alarm blares and an incident unfolds, a well-oiled response machine is crucial.
Let’s take an in-depth look at the incident response and mitigation practices within SOCs, exploring effective strategies and the critical collaboration between SOCs and stakeholders during security breaches.
Incident response strategies in Security Operation Centers
SOCs employ sophisticated incident response strategies to quickly identify, analyze, and mitigate security threats, ensuring minimal disruption to business operations.
Here are the critical steps taken by the SOC team to provide efficient incident response.
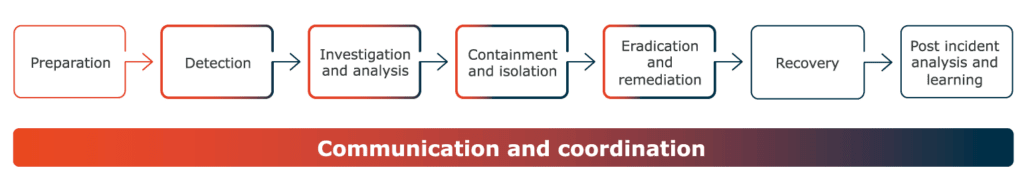
Preparation
The foundation of effective incident response lies in meticulous preparation. SOCs establish comprehensive incident response plans that outline roles, responsibilities, and procedures to be followed during a security incident. This includes defining the severity levels, establishing communication protocols, and conducting regular training exercises to ensure readiness.
Detection
Rapid detection is key to minimizing the impact of security incidents. SOCs leverage advanced technologies such as Security Information and Event Management (SIEM) systems, intrusion detection systems, and threat intelligence feeds to monitor network traffic and identify anomalies.
Investigation and analysis
Once an incident is detected, thorough analysis is conducted to understand the nature and scope of the threat. The SOC team also gathers evidence, identifies the attack vector, and tries to understand the attacker’s motives and goals. This deep dive feeds into subsequent mitigation and remediation efforts.
Containment and isolation
After analyzing the incident, SOCs move swiftly to contain the threat and prevent its further spread. This may involve isolating affected systems, shutting down network segments, blocking malicious activities, disabling user accounts, and implementing corrective measures.
Eradication and remediation
With the attack’s nature understood, the SOC may eradicate the malware or malicious code and restore affected systems to their clean state. The goal is to eradicate the root cause of the incident and prevent it from recurring.
Communication and coordination
Clear and effective communication is paramount during incident response. SOCs maintain open lines of communication within their teams and establish communication protocols with external stakeholders, including clients. Coordination between different teams within the SOC ensures a cohesive and efficient response to security incidents.
Recovery
Once the threat is contained and eradicated, the focus shifts to recovery. SOCs work to restore affected systems to normal operation, ensuring minimal disruption to business processes. This phase includes validating the integrity of restored systems and implementing lessons learned to enhance future incident response capabilities.
Post-incident analysis and learning
Incident response is a continuous learning process. SOCs conduct thorough post-incident analyses to identify weaknesses in their response strategies and areas for improvement. This information is used to update incident response plans, enhance detection capabilities, and strengthen overall security posture.
Collaborating with SOC stakeholders during incidents
Effective incident response isn’t a solo act. A crucial element is the seamless collaboration between SOCs and their stakeholders. The relationship between a SOC and its stakeholders should be characterized by transparency, communication, and mutual understanding. Below are some best practices for effective collaboration during security incidents.
Timely communication
SOC teams must establish transparent and clear channels of communication with clients to provide timely updates on ongoing incidents. This includes sharing relevant information about the nature of the incident, the potential impact, and the steps being taken to mitigate the threat. Regular updates, even amidst the storm, build trust and confidence, and demonstrate the SOC’s commitment to addressing the situation.
Joint incident response plans
Pre-defining incident response plans is key. These plans, crafted jointly by SOCs and stakeholders, outline roles and responsibilities, communication protocols, and escalation procedures. Having a playbook in place ensures a coordinated and efficient response when an attacker strikes.
Joint incident analysis
Collaboration extends to jointly analyzing incidents with clients. This involves sharing insights into the attack vectors, the compromised systems, and the potential implications for the organization. By involving stakeholders in the analysis process, the SOC team gains valuable context and the client gains a deeper understanding of the incident.
Customized mitigation strategies
Every organization is unique, and so are its cybersecurity needs. Collaborative incident response involves tailoring mitigation strategies to the specific environment and requirements of the stakeholders. This may include implementing additional security measures, adjusting configurations, or providing recommendations for improving overall cybersecurity resilience.
Client input in decision-making
While SOCs possess the expertise to handle the technical aspects, critical decisions require stakeholder’s input. Effective collaboration recognizes the client’s expertise and incorporates their input into the decision-making process. Stakeholders may have valuable insights into their systems and business processes, and their input can contribute to more informed and effective incident response decisions around critical choices, such as when to resume operations, whether to notify authorities, or whether to engage external forensic investigators.
Realistic examples of collaboration in incident response
Let’s illustrate these collaboration best practices with several realistic scenarios.
Phishing incident
Imagine a scenario where a SOC detects a potential phishing attack targeting an organization’s employees, or that a client reports receiving suspicious emails. The SOC quickly analyzes the emails, identifies them as phishing attempts, and blocks them across the organization’s network, preventing the spread of the phishing campaign.
In this case, effective collaboration also involves working together to implement user awareness training to prevent future attempts.
Ransomware attack
In the event of a ransomware attack, collaboration becomes even more critical. A client’s system is encrypted and a ransom demand appears. The SOC immediately works with the client identifying the compromised system and isolating it, analyzing the malware, and identifying decryption options. The SOC and the affected organization then work together to assess the extent of the ransomware infection and decide on the appropriate course of action going forward.
Beyond isolating infected systems this may involve restoring data from backups and negotiating with threat actors if necessary. Throughout the process, constant communication and joint decision-making ensure a coordinated response, especially since the ultimate decision will usually require balancing financial impact with data sensitivity.
Insider threat incident
An insider threat incident requires a delicate balance between protecting sensitive information and addressing potential personnel issues. In this scenario, the SOC collaborates closely with the affected organization’s internal teams, including HR and legal. Together, they investigate the insider threat, determine the scope of unauthorized access, and take appropriate actions which may include terminating access, legal action, or implementing additional security controls.
Zero-day attack
A zero-day attack exploits a previously unknown vulnerability. The SOC, leveraging threat intelligence feeds, quickly detects the anomalous activity and takes immediate action to contain the spread. The SOC keeps the client informed about the ongoing investigation and works with the vendor to develop a patch for the vulnerability.
Summary
Incident response and mitigation in SOCs are multifaceted processes that demand a combination of technological prowess, strategic planning, and effective collaboration with clients. As attackers evolve their tactics, SOCs must constantly refine their incident response and mitigation practices. SOCs, as the guardians of digital assets, must not only respond swiftly to security incidents but also foster partnerships with the organizations they protect.
By embracing transparency, communication, and joint decision-making, SOCs and their clients can navigate the complex landscape of cybersecurity incidents with resilience and agility, ensuring that digital defenses remain strong in the face of evolving threats.

