ABOUT US
Cytek Security provides state-of-the-art cybersecurity solutions, delivered by the world’s top cyber experts. This includes advisory and implementation services, managed security services, and capability building.
As a global company operating in 14 diverse locations and spanning numerous business domains (including technology, real estate management, hospitality, and finance), YNV Group faces a constantly evolving and intricate landscape of cyber risks. That’s why YNV Group trusts Cytek to provide critical cybersecurity services, from planning and implementation to round-the-clock monitoring and support.
Cytek adheres to the foundational cybersecurity CIA triad model (Confidentiality, Integrity, and Availability) to assess risks, shape policies, and ensure robust protection and security for YNV Group.
- Confidentiality: Safeguarding sensitive information is paramount for organizations like YNV Group. Cyber risks that threaten confidentiality often involve unauthorized access to data, which can occur through data breaches, insider threats or hacking attempts. The compromise of confidential data can result in severe financial losses, reputational damage, and legal liabilities. Maintaining confidentiality is therefore a cornerstone of our cybersecurity efforts for YNV Group.
- Integrity: Cyber risks include targeting the integrity, accuracy and trustworthiness of data. These risks include data manipulation, unauthorized changes, and the introduction of information-altering malware. When data integrity is compromised, an organization like YNV Group could end up making decisions based on inaccurate information, leading to financial and operational consequences. Therefore, upholding data integrity is crucial for making informed business decisions.
- Availability: Ensuring the continuous availability of systems and data is essential for business continuity. Cyber risks that aim to disrupt availability include distributed denial-of-service (DDoS) attacks, ransomware, and system failures due to vulnerabilities. These attacks can disrupt operations – causing downtime, financial losses, and damage to YNV Group’s reputation. Hence, maintaining the availability of critical systems and data is a primary focus of our cybersecurity efforts.
We apply the CIA triad model because cyber risks can impact all three (or a combination) of CIA principles simultaneously. For instance, in real estate management, ensuring the availability of Building Management Systems (BMS) is essential, while maintaining their integrity is crucial to guarantee that elevators, ventilation systems, and doors operate as intended. In financial services, confidentiality takes precedence, and IT services security managers must prioritize all aspects of data security.
Different lines of business require varying security expertise, leading to divergent security priorities. Challenges in securing a diverse multinational group also stem from unique attack vectors, specific technology needs, varying infrastructures, complex governance meeting national data standards, and management of multiple time zones.
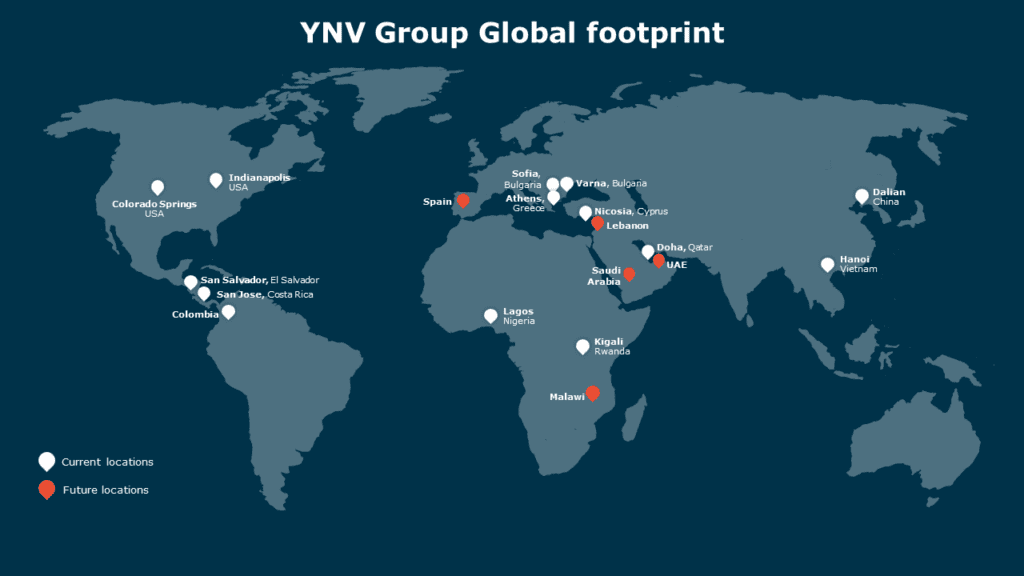

To address these challenges, organizations like YNV Group need a multidimensional approach that considers time, geography, and business needs. This approach demands diverse security expertise while maintaining a unified cybersecurity posture within a Security Operations Center (SOC) and a unified operational framework.
The Solution
Cytek adopts a comprehensive approach to protect data and systems. We utilize a blend of proactive and responsive cybersecurity strategies to adeptly navigate evolving cyber threats, while upholding the principles of CIA. We firmly assert that robust cybersecurity starts with mastering the basics. This encompasses employing access controls to safeguard confidentiality and integrity, utilizing data encryption for confidentiality, implementing backups for availability assurance, establishing well-structured incident response plans for swift mitigation, and engaging in meticulous threat hunting as a proactive measure.
To safeguard the YNV Group and its customers worldwide, we’ve implemented a comprehensive global security infrastructure leveraging technology, human expertise, and established procedures.
Technology:
- Employing a decentralized Security Operations Center (SOC) following the ‘follow the sun’ model.
- Our SOC is powered by cutting-edge AI-enabled infrastructure and is equipped with proven proprietary playbooks.
- Incorporating threat intelligence as a standard practice.
- We possess robust in-house architectural and implementation capabilities.
- Utilizing top-tier cybersecurity solutions enhanced by our unique optimization features.
People:
- Our seasoned management team brings a wealth of nation-grade expertise to the table.
- Expert cyber teams are specialized in various cybersecurity disciplines.
- We maintain both proactive and reactive capabilities, encompassing threat hunting and incident response.
- Continuous training keeps us at the forefront of the ever-evolving cyber landscape.
Procedures:
- We have meticulously crafted playbooks, procedures, and protocols to oversee the entire organization from our centralized SOC.
- Seamless handoff procedures, team transfer protocols, synchronization, and information exchange mechanisms are in place.
- Our approach emphasizes cross-practice collaboration, involving IT, Cyber, and Operations.
- Leveraging extensive cyber intelligence enhances our security posture and ensures effective threat management.
Bottom Line
For numerous years, Cytek has effectively safeguarded both YNV Group’s enterprises and their clientele from a multitude of threats. This same level of protection is extended to our broader customer base through services such as Advisory & Implementation, Managed Security Services, and Cybersecurity Capability Building.